An edited version of this article was previously published on Forbes.
Passwords could soon be consigned to history books. Apple’s introduction of WebAuthn-based passkeys with the latest versions of its MacOS and IOS operating systems means that users can rely on FaceID-like technology to log in to online accounts. This is a drastic improvement over existing online identity management options, but passkeys still will not hand us complete control over our own online identities. For that to happen, we need to look at Self-Sovereign Identity (SSI).
Passkeys enhance security, but our online behavior privacy remains under threat. Even if you apply passkey technology to single sign-on, every online action could be logged by the Identity Provider (IDP), adding to your behavioral pattern. An IDP, theoretically, could track and analyze such patterns enabling it to reverse-engineer its way to identifying you, even selling your data.
Self-Sovereign Identity removes all personal information from centralized locations and puts it back in the hands of each one of us. The central tenet of SSI is that everyone has a moral right to be in control of their identity – meaning: It should be up to each of us to decide whether to share private information with any entity for authentication, and should one decide to pursue authentication, what to share and when to share it. No silos of personal data are created. In other words, both attributes and credentials, which can be self-signed or signed by third parties, must be controlled only by users, who present their data to Service Providers (SPs) whenever they desire.
With SSI, a secure and digital peer-to-peer channel is established between ID Issuer, ID Owner and ID Verifier. The ID Owner – i.e., the user – chooses which attributes of their identity they want to “show” to the ID Verifier. Successfully implemented, SSI would provide open access, convenience, immutability, decentralization, lock-tight security and, crucially, individual control – as verification happens without revealing anything sensitive and on the ID owner’s terms.
A proposed vaccine verification method, which we’ll describe below, illustrates how it could work.
In 2016, Christopher Allen defined the 10 guiding principles of Self-Sovereign Identity thus:
- Existence: The user must exist independent of any service provider/identity provider.
- Control: The user must control their identities.
- Access: The user must always have access to their data.
- Transparency: All systems and algorithms must be transparent to the user.
- Persistence: Identities must be persisted.
- Portability: The services and information about the user’s identity must be transportable.
- Interoperability: Identities should have as wide a range of use as possible across different systems.
- Consent: The user must always consent to the usage of his identity data.
- Minimization: When necessary to show some information, always show as little as possible to accomplish the task.
- Protection: Users’ rights must be protected.
The two main ingredients of SSI are Verifiable Credentials (VCs) and Decentralized Identifiers (DIDs).
Verifiable Credentials
Per W3C, “Verifiable credentials represent statements made by an issuer in a tamper-evident and privacy-respecting manner.
True to the Zero-knowledge proof (ZKP) model, which we discussed in a previous article, this enables physical credentials to be digitized, and holders can selectively disclose specific information from this credential without exposing the actual data (such as proving that you are old enough to buy wine without revealing your date of birth or proving that you are licensed to ride a motorcycle without disclosing your name or address.)
Decentralized Identifiers
A key part of SSI, decentralized identifiers (DIDs) enable verifiable, decentralized digital identity by creating a unique, private and secure peer-to-peer connection between two parties.
So how would it work? In a scenario described by Tykn, the government could use DIDs to issue a digital version of your passport. You would go to your local office where you would scan a QR code to exchange DIDs and create a secure connection. The clerk would use the secure connection to issue your digital passport in the form of a Verifiable Credential, which you then store in your digital wallet, enabling you to produce it to a verifier upon request, right from your smart device.
Blockchain
In most cases, SSI involves blockchain. Through the infrastructure of a blockchain, the verifying parties do not need to check the validity of the actual data in the provided proof but can rather use the blockchain to check the validity of the attestation and attesting party.
To make this work, issuing authorities of, for example, passports, drivers’ licenses, financial information or medical records, would provide information to the government or other entity which would then be cryptographically secured on a blockchain using a hash function.
In our previous article, we discussed the “Corona passport” used in Denmark as a form of ZKP in action. Though not an example of true Self-Sovereign Identity, this passport does provide some level of DID as the end user can choose whether to have the passport display certain details. In their February 2022 research paper Leveraging Self-Sovereign Identity, Blockchain, and Zero-Knowledge Proof to Build a Privacy-Preserving Vaccination Pass, Mauricio de Vasconcelos Barros, Frederico Schardong and Ricardo Felipe Custódio propose a method that takes this idea much further by using SSI, ZKP and blockchain to enable a versatile and easily implemented vaccine authentication system that could be used universally. A system that would allow a person to prove vaccination status without revealing the vaccine producer or when or where they were vaccinated.
The first part of the proposed system is a public or private entity authorized to administer vaccines being registered on the blockchain to issue VCs for vaccinated people. The VC, which is sent immediately following the vaccination, details the vaccinee’s name, date of birth, the laboratory that produced the vaccine, the applied dose and the date it was administered. The vaccinee stores the VC in a digital wallet – such as a smartwatch or a smartphone app – ensuring that no personal information is stored on the blockchain.
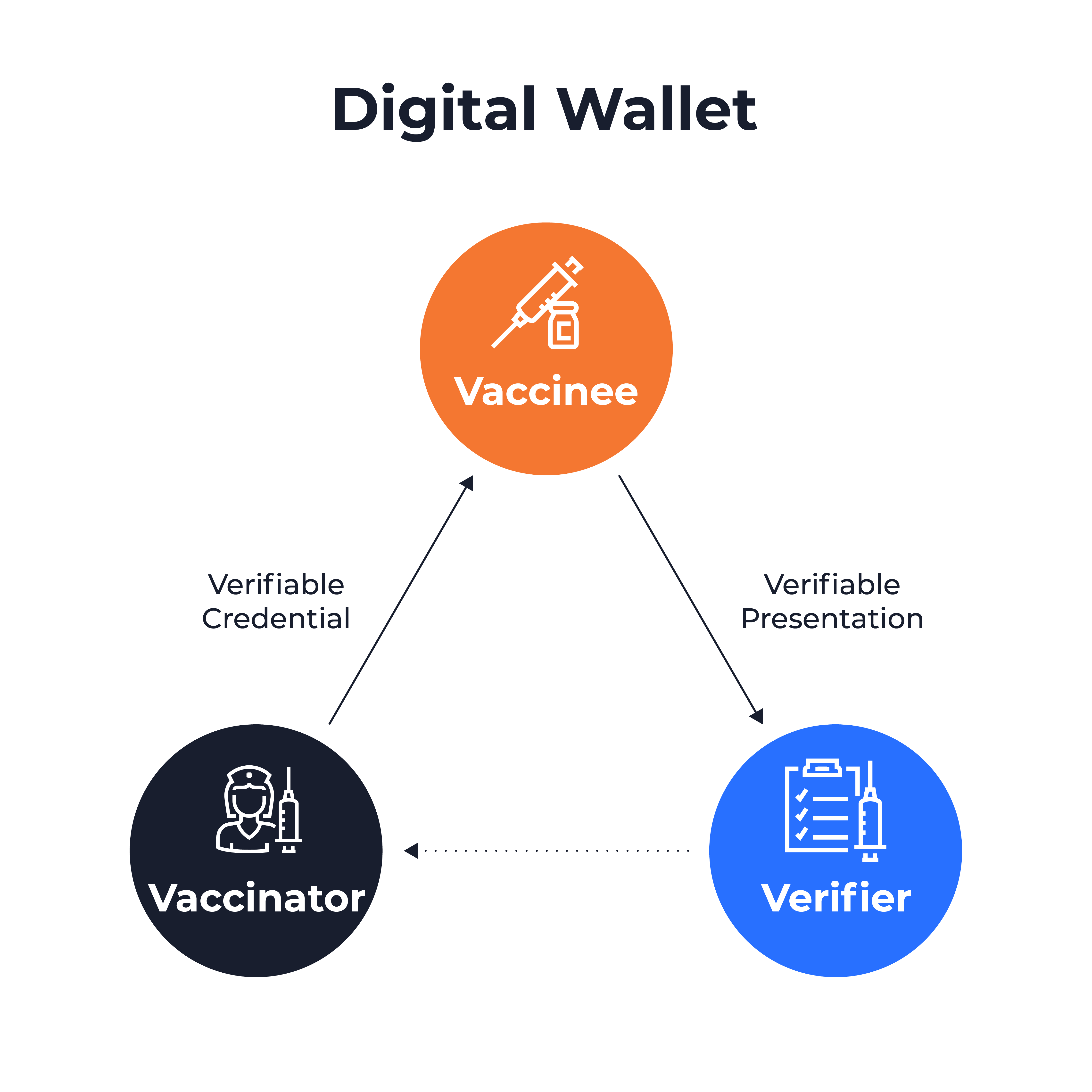
At any time, the vaccinee can produce a VP using the digital wallet to prove their vaccination status to a verifier. The user can customize the amount of personal data included in the VP. For example, if the vaccinee prefers not to disclose the maker of the vaccine, they can create a VP using ZKP to prove that the value of the laboratory field on the VC matches one of the values in a list of laboratories accepted by the verifier.
Alternatively, the verifier might define the VP format based on specific requirements for a given use case. The verifier would then send the VP request to the vaccinee who – again using the digital wallet – can accept and produce a VP in the requested format.
This is a perfectly feasible example of how blockchain- and ZKP-based self-sovereign identity could help us hit the sweet spot where personal ID control, complete privacy and decentralization deliver maximum convenience and peace of mind.
So, while Apple’s passkeys are a giant step forward for privacy and security in the age of Open Data, it holds nowhere as much promise as the Web 3.0 concept of Self-Sovereign Identity. When – in a not-too-distant future, hopefully – SSI can be applied to a broad range of daily-life use cases, it will not only further eliminate threats to our behavior privacy – but it will also hand us complete control of our identities. Your ID managed right from your fingertips – tapping your digital wallet.
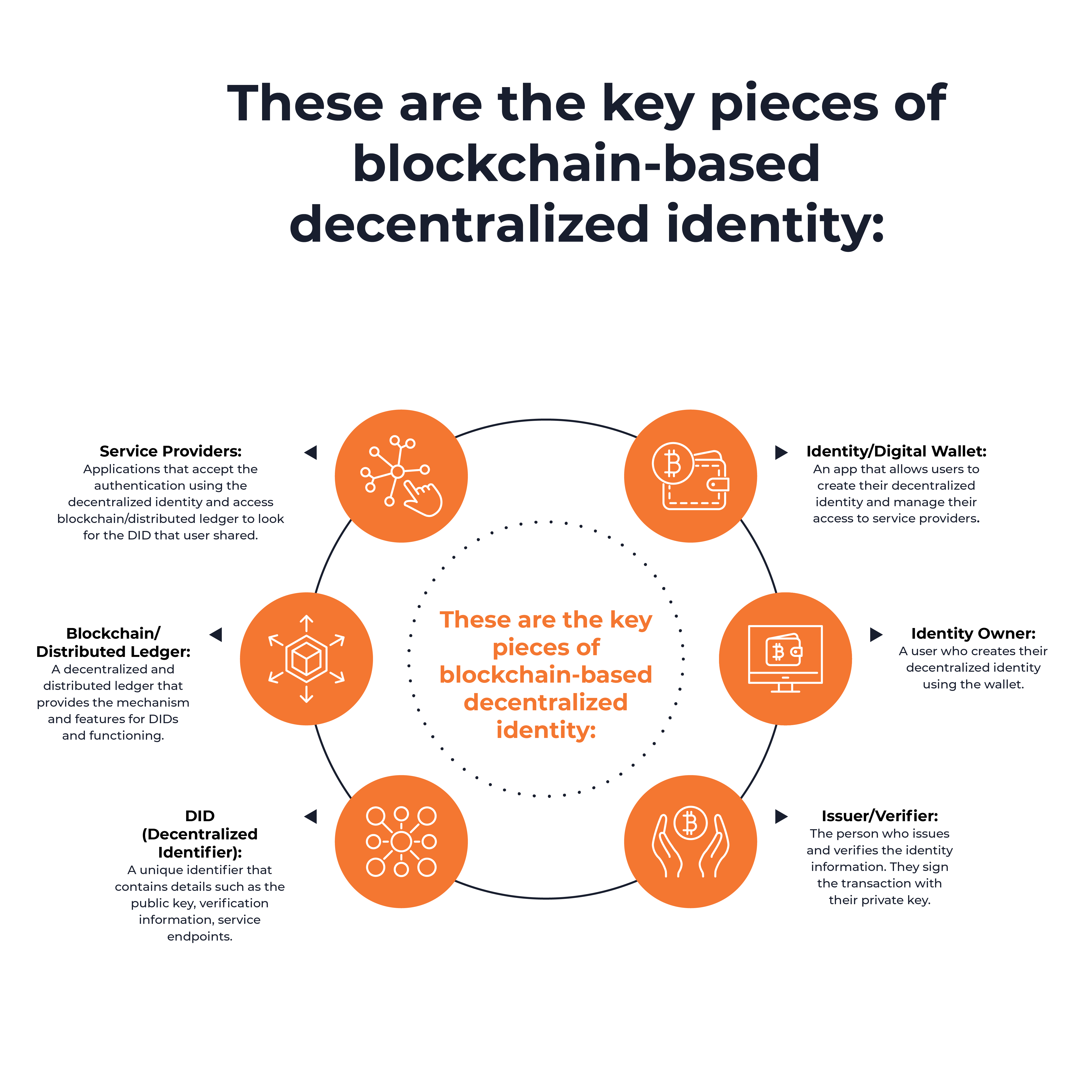
These are the key pieces of blockchain-based decentralized identity:
- Identity/Digital Wallet: An app that allows users to create their decentralized identity and manage their access to service providers.
- Identity Owner: A user who creates their decentralized identity using the wallet.
- Issuer/Verifier: The person who issues and verifies the identity information. They sign the transaction with their private key.
- Service Providers: Applications that accept the authentication using the decentralized identity and access blockchain/distributed ledger to look for the DID that user shared.
- Blockchain/Distributed Ledger: A decentralized and distributed ledger that provides the mechanism and features for DIDs and functioning.
- DID (Decentralized Identifier): A unique identifier that contains details such as the public key, verification information, service endpoints.